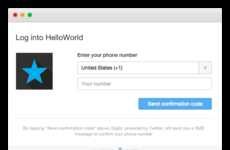

Two-step verification minimizes threat potential
Implications - While many consumers are favoring streamlined verification methods, others are leaning toward two-factor authentication to enhance security. These multi-step processes rely on extra data, personalization and even biometric measures to provide greater protection and minimize potential for attack. This shift indicates that, in this modern age, information is considered the most sensitive currency, and consumers and businesses alike are willing to take extra precaution to avoid leakage.
Workshop Question - How are you ensuring consumer trust in an age of digital parnaoia?
Trend Themes
1. Multi-factor Authentication - Consumers and businesses are willing to take extra precautions to avoid the leakage of sensitive information.
2. Biometric Technology - Innovative authentication assessment systems are using biometric technology to continuously monitor online activity.
3. Password-free Login - Companies are moving beyond the password to offer more efficient and frustration-free login options.
Industry Implications
1. Cybersecurity - Developments in multi-factor authentication and biometric technology offer great disruptive innovation opportunities in the cybersecurity industry.
2. Mobile App Development - The trend towards password-free login options presents new opportunities for companies specializing in mobile app development.
3. Financial Technology - The need for enhanced security measures in financial technology creates opportunities for companies to develop multi-factor authentication and biometric technology solutions.
4 Featured, 31 Examples:
72,479 Total Clicks
Date Range:
Nov 14 — Oct 15
Trending:
Untested
Consumer Insight Topics: